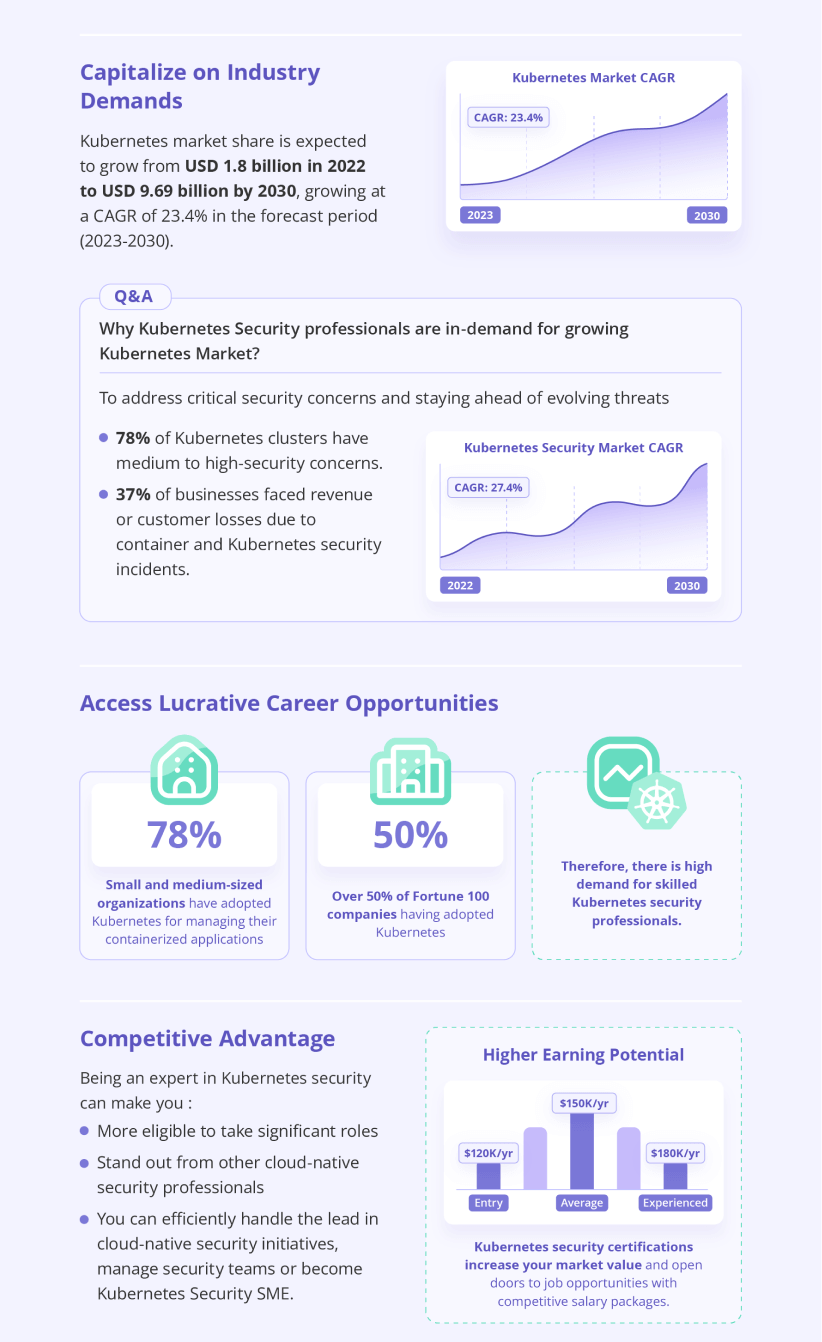
Employers worldwide are looking for candidates with a greater comprehension of securing Kubernetes from threats that are becoming more clever and technologically advanced. In the context of that, let us explain why you should learn Kubernetes security in 2024
Learn Kubernetes Security in 2024
Learning Kubernetes can level up your career and help you to stand out to potential employers and organizations. By upskilling in Kubernetes security, you can gain a deeper understanding of the platform’s architecture, network security, identity and access management, and other essential security best practices.
Here are some reasons why you should learn Kubernetes security
In-Demand Skill
As Kubernetes gains popularity, so does the need for Kubernetes security experts.
Career Growth
Becoming a Kubernetes security expert opens doors to leading cloud-native security projects, managing security teams, and becoming a Kubernetes Security Subject Matter Expert (SME).
Competitive Edge
Gain a competitive advantage in the cloud-native field with specialized security skills.
Also Download, Learn Kubernetes Security PDF Free E-book
Personal Growth
Learning Kubernetes security enhances critical thinking, problem-solving, and research abilities, keeping you up-to-date with the latest security practices.
Also Read, Best Kubernetes Security Books
Higher Earnings
Kubernetes security certifications can boost your resume, leading to job opportunities with competitive salaries and benefits.
Why Organizations are Increasingly Seeking Kubernetes Security Professionals Now?
Hiring employees with a deep understanding of Kubernetes security can help companies to meet compliance requirements, protect against security risks, and reduce costs associated with remediation and recovery. Proper Kubernetes security measures can help organizations maintain their reputation and trust, enabling continuous deployment and innovation.
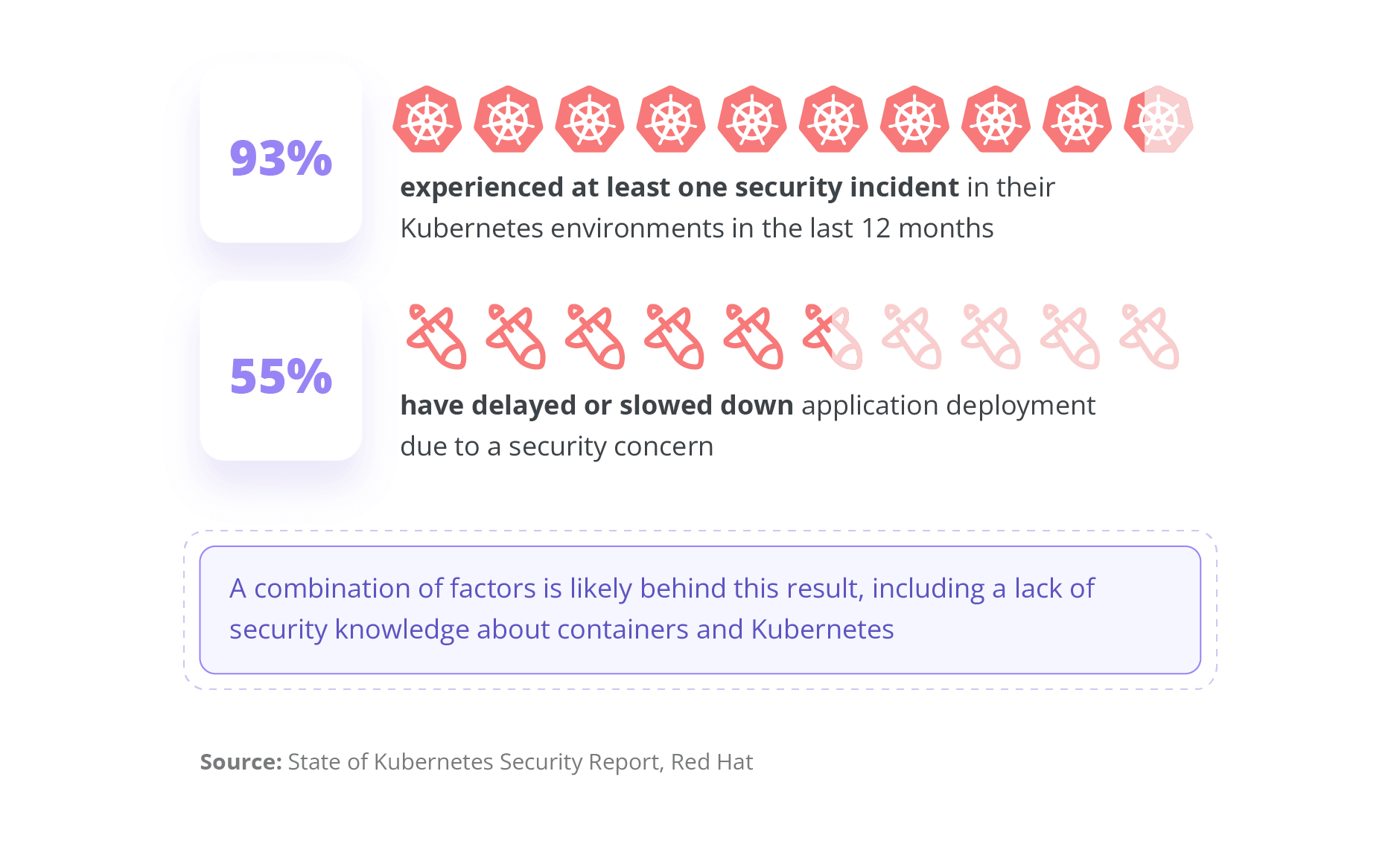
Here are 3 major reasons why organizations hire individuals skilled in Kubernetes security
To Meet Compliance Requirements:
Professionals who are skilled in Kubernetes security can help organizations to be consistent in ensuring their containerized applications meet compliance requirements. There are specific compliance requirements that organizations have to meet, such as GDPR, PCI-DSS, and HIPAA. These compliance requirements ensure organizations implement specific security controls to protect sensitive data.
Understanding the Security Risks in Kubernetes:
Kubernetes is a complex platform, and there are many security risks associated with it. Organizations need more skilled employees to identify and mitigate these risks.
Avoid Delays in Development and Deployment Due to Security Issues:
Having employees skilled in Kubernetes security helps organizations to ensure that their containerized applications development and deployment are not slowed down due to security reasons.
“In the cloud-native era, Kubernetes has become the de facto standard, with a variety of commercial platforms available on the market. Organizations are increasingly deploying large-scale analytics and AI workloads in containerized environments. While containers provide many benefits, the transition to containers is very complex. As a result, in 2023, the main bottleneck to container adoption will be the shortage of talent with the necessary skill set for tools like Kubernetes.”
Haoyuan Li, Founder and CEO of Alluxio
Kubernetes Security Roadmap for 2024
Mastering Kubernetes security requires a solid foundation in Kubernetes itself and then specializing in security concepts and best practices. Here’s a roadmap to guide you in 2024:
Phase 1: Kubernetes Fundamentals (1-2 months)
- Basics: Get comfortable with core Kubernetes concepts like pods, deployments, services, namespaces, etc. Resources like kubernetes.io official documentation, interactive tutorials like Katacoda, and online courses on Udemy or Coursera can help.
- Networking: Understand Kubernetes networking, CNI plugins, service types, ingress, and network policies. Explore resources like Kubernetes in Action and Kubernetes Network Policies Cookbook.
- Storage: Learn about Kubernetes storage types (PersistentVolumes, CSI), dynamic provisioning, and access control mechanisms. Use books like Kubernetes: Up and Running for deeper understanding.
- Security Principles: Build a strong foundation in general security principles like authentication, authorization, access control, secrets management, and vulnerability management. Refer to OWASP Top 10 for a holistic view.
Phase 2: Deep Dive into Kubernetes Security (2-3 months)
- Pod Security Policy (PSP): Understand PSP’s role in restricting container privileges and capabilities. Learn how to define and enforce PSPs using YAML specifications and tools like Kustomize. Resources like Kubernetes official documentation and blog posts are helpful.
- Network Security: Dive deeper into Kubernetes network security with tools like Calico or Cilium. Understand how to implement network segmentation, pod isolation, and service mesh for secure communication. Utilize resources like the Calico documentation and Cilium documentation.
- Secrets Management: Explore secure ways to store and manage secrets like API keys, passwords, and certificates in Kubernetes. Tools like Vault, Kubernetes Secrets Store CSI driver, and Sealed Secrets are popular options. Refer to documentation of these tools and related blog posts.
- Admission Control: Learn about Kubernetes admission controllers that validate and potentially reject resource requests before they are created. Understand Webhook admission controllers and tools like OPA Gatekeeper for advanced security policies. Use official documentation and GitHub repositories for these tools.
Also Read, Best Tools for Kubernetes Security
Phase 3: Advanced Kubernetes Security (1-2 months)
- Security Auditing and Logging: Implement practices for auditing Kubernetes activity, analyzing logs for suspicious events, and implementing alerting mechanisms. Use tools like Falco, Sysdig Secure, and ELK Stack for comprehensive monitoring. Refer to their documentation and case studies.
- Threat Detection and Response: Get familiar with common Kubernetes security threats like supply chain attacks, privilege escalation, and container image vulnerabilities. Learn about tools like Sysdig Secure, Aqua Security, and StackRox for threat detection and mitigation. Explore relevant case studies and white papers.
- Compliance and Governance: Understand compliance requirements for deploying and operating Kubernetes workloads, such as PCI-DSS, HIPAA, and SOC 2. Learn how to configure Kubernetes and related tools to meet compliance standards. Official documentation and resources from compliance bodies are essential.
- Continuous Security and Automation: Integrate security practices into your CI/CD pipeline for automated vulnerability scanning, image signing, and security policy enforcement. Tools like Anchore, Snyk, and Trivy can help automate security checks. Refer to their documentation and best practices guides.
Also Read, Kubernetes Security Best Practices
Additional Tips to Learn Kubernetes Security
- Hands-on practice: Set up a Kubernetes cluster (minikube, kind, or cloud-based) and implement the security concepts you learn.
- Stay updated: Follow blogs, newsletters, and communities like Kubernetes Security Special Interest Group (SIG-Security) for latest security updates and best practices.
- Network with experts: Join online forums, attend conferences, and connect with other Kubernetes security professionals to learn from their experiences.
Also Read, Best Kubernetes Books
How to Get Kubernetes Security Training?
You can get trained in Kubernetes security by enrolling in our Cloud-Native Security Expert (CCNSE) course, which provides hands-on training in important concepts such as
Hacking Kubernetes Cluster, Kubernetes Authentication and Authorization, Kubernetes Admission Controllers, Kubernetes Data Security, Kubernetes Network Security, Defending Kubernetes Cluster
Course Highlights:
- 50 + guided exercises uniquely designed by industry experts
- 24/7 instructor support
- Browser-based labs for hands-on training
- Lifetime access to course manuals and videos
“According to Red Hat survey, 43 percent consider DevOps as the role most responsible for Kubernetes security.“
Download Free E-books on Kubernetes Security 101





0 Comments