Loren Kohnfelder and Praerit Garg, two engineers from Microsoft, came up with STRIDE in the 1990s. Till now, STRIDE remains to be the concept most security professionals use, being proactive in discovering and fixing vulnerabilities.
The model, therefore, allows for the systematic assessment of security risks at every stage of the whole development process and hence offers great insights at each stage valuable for making effective decisions.
This blog delves deeper into the in-depth understanding of what is a STRIDE Threat Model, its classification, and the benefit that one might accrue.
Also read about Threat Modeling in Practice
What is a STRIDE Threat Model?
Stride full form:
The full form of “STRIDE” in the context of security is a mnemonic representing a model used to identify computer security threats. It stands for:
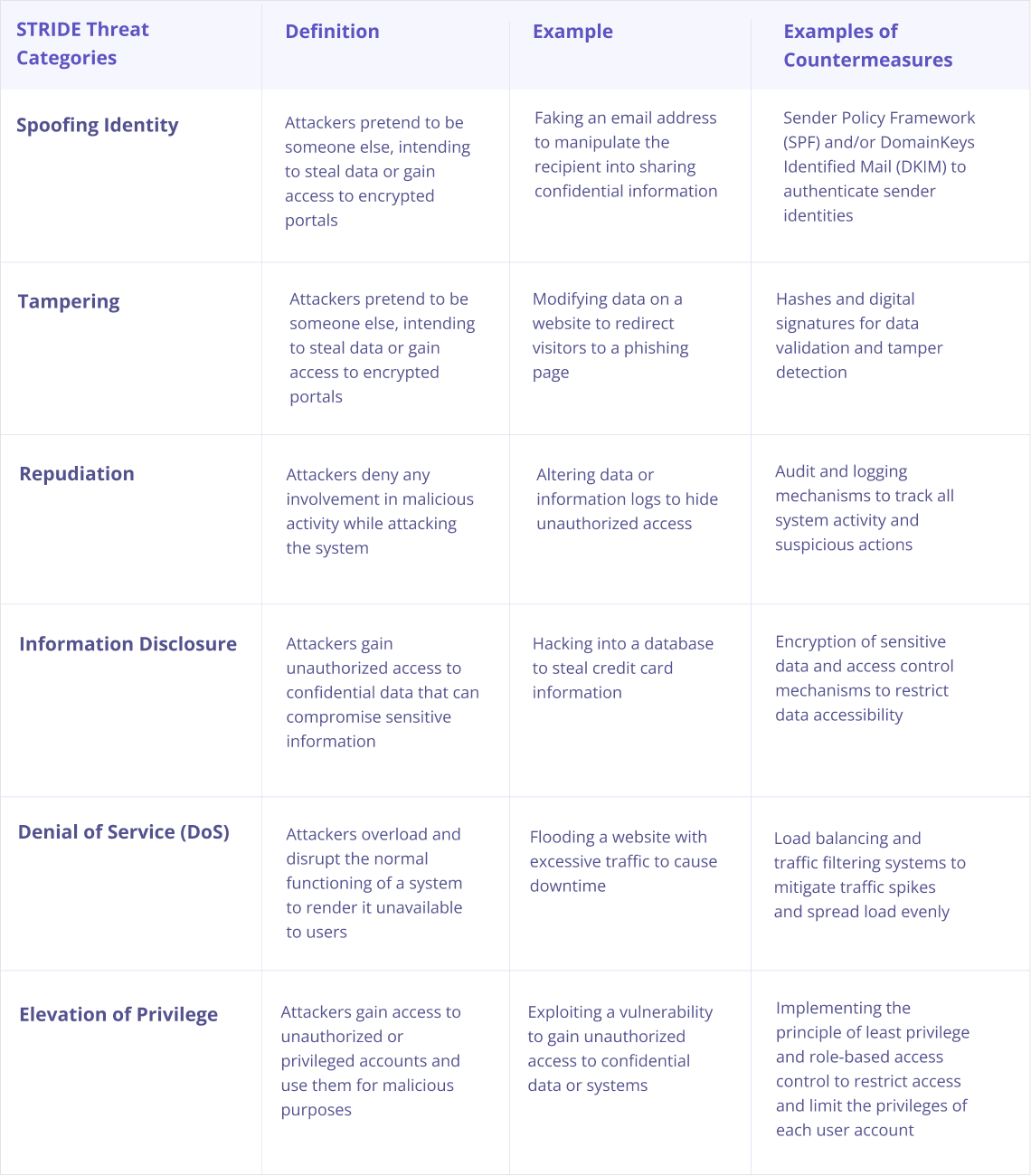
- Spoofing identity
- Tampering with data
- Repudiation
- Information disclosure
- Denial of service (DoS)
- Elevation of privilege
The STRIDE threat model is a developer-focused model to identify and classify threats under 6 types of attacks – Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service DoS, and Elevation of privilege. This model is one of the most commonly used threat modeling methodologies as its model provides important insights to be proactive in recognizing and defending important system infrastructure, devices, and networks that are susceptible to attacks.
STRIDE steps include: finding the threats inherent in the design of the system and implementing contingencies to cover those gaps.
Moreover, The STRIDE threat model ensures that software products maintain the CIA triad. That is confidentiality, integrity, and availability. In fact, STRIDE’s designers-Microsoft, developed this framework because the developers were ignorant. And the company wanted them to think about security and threats while designing and developing their software.
Also read about Threat Modeling Vs Penetration Testing
Understanding Threat Classification in the STRIDE Threat Model
The STRIDE Threat methodology puts forward a framework that demands to identify and classify threats or vulnerabilities in the following classification:
Spoofing Identity
Many times, during identity spoofing, a hacker takes over a spoofed identity with a single goal of luring your information into theft or gaining access to some highly secured and well-encrypted portals that are beyond his or her means. For example, identity spoofing in STRIDE and threat modeling may be as simple as an email sent out from a different email address to pretend to be sent by the said entity, hence fooling the recipient about its data and authentication.
Spoofing by an attacker can come in the forms of DNS spoofing, ARP spoofing, DNS compromise, and IP spoofing.
Tampering
Tampering involves the attacker or hacker manipulating, removing, or modifying important data to attack a system or network. In fact, tampering is an attack on the integrity of the information system. This helps a malicious third-party hacker to enter and modify systems that are encrypted or authenticated only for a few authorized persons in an organization.
Example: Some of the common examples of tampering that can cost hugely include tampering with a configuration file to gain system control, making threatening changes, or removing a log file and inserting a malicious file.
Repudiation
A repudiation threat involves a bad actor attacking the system without accepting their involvement in such malicious activity. Mostly in Repudiation attacks, the system does not have the ability to identify the actor or attacker. To summarize, a repudiation attack happens when software, network, or a system does not take the necessary controls.
Example: An attack to change the data provides authorization that enables to log of wrong data to log files.
Information Disclosure
Information disclosure refers to the unauthorized release of confidential information. This security vulnerability can have significant repercussions on the processes, data, and storage of information within a website or application. And In addition, can potentially compromise sensitive information.
Example: Some common examples of information disclosure threats include the exposure of source code files through temporary backups, error messages, and the accidental revelation of background information.
Denial of Service ( DoS)
In denial of service (DoS), the strategy is overwhelming with excess traffic in one particular system to the saturation point of its normal function, hence causing disruption. This actually causes costly downtimes and great losses to the victims. DoS attacks operate at both the application and network layers. Besides, they are becoming increasingly common and sophisticated. To mitigate the impact from both network and application layers, firewalls are often used as a defense mechanism.
Example: Flooding a website with excessive traffic to cause downtime.
Elevation of Privilege
Privilege Elevation occurs when an attacker bypasses security measures to gain unauthorized access or to elevate their access rights within a system, typically by exploiting vulnerabilities. It enables attackers to steal, manipulate, or exploit data for their own benefit.
A simple example would be an attacker initially limited to reading a file, finding multiple ways to modify system settings to gain the ability to edit that specific files and potentially access more files in the same directory.
Also read, Threat Modeling vs Pentesting: What is the Difference?
Top 5 Benefits of the STRIDE Threat Model
STRIDE threat modeling methodology is a very useful methodology that helps to decrease the chances of vulnerabilities and threats to exploit a system or network. Following are the top 5 benefits of the STRIDE threat model.
- The STRIDE Threat Model lays strong insights and vision for a larger security program.
- Helps to avoid vulnerabilities and threats from an early stage
- Cost-effective compared implementation to alternative threat modeling methodologies.
- The STRIDE Threat Model provides a brilliant checklist for a secure software development lifecycle.
- It Is an effective model for exercising threat modeling methodology at regular intervals and its outcome can combine with the DREAD risk assessment model which helps to prioritize and tackle action against different threats and vulnerabilities.
Also read, Why DevSecOps is a promising career option?
How STRIDE Helps in Cloud Security?
STRIDE threat modeling methodology helps to counter emerging threats to cloud computing. There is a need to assess systems to avoid cyberattacks constantly. In fact, Cloud computing is becoming increasingly popular in the corporate world. And On-premises computing is now free from many vulnerabilities and threats when cloud computing is combined with needed security.
In order to fight malicious behavior, you must use strategies like the STRIDE threat model. This helps to improve awareness of different threats. For example, it will uncover the need for monitoring, logging, and alerts. Also, you should eliminate the threats by strengthening authentication and developing data protection safeguards.
And it is important to ensure Confidentiality and availability and protect against cyberattacks. Moreover, STRIDE helps to rank the emerging threats in priority. They also help to analyze how easily threats can reproduce, their overall impact, etc.
You can use IoT devices to identify threats and existing vulnerabilities in your systems. However, by using a STRIDE threat model to identify risks, you can continue protecting IoT devices from security flaws.
What are Threat Modeling Template?

The threat modeling template is a structured approach to identify and mitigate potential security risks in software systems. It involves several steps, including defining the scope, identifying assets, analyzing threats, and implementing mitigations.
You can download our FREE Agile Threat Modeling PDF Guide
Stride Threat Modeling Data Flow Diagrams

Threat modeling is a crucial process in identifying and mitigating potential security risks in software systems. The Stride Threat Modeling Data Flow Diagrams template provides a structured approach to systematically analyze and document the security threats associated with your application’s architecture and design.
Stride Security Threat Model
The STRIDE security threat model is a widely used framework for identifying threats and classifying potential security threats in software systems. Developed by Microsoft in the late 1990s, it categorizes threats into six types: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege.
This model helps ensure that software meets the CIA triad of Confidentiality, Integrity, and Availability. It is particularly useful for identifying and mitigating threats in cloud computing and IoT devices, and is often used in conjunction with other threat modeling methodologies.
Also read, 10 Types of Threat Modeling Methodology to Use in 2024
Conclusion
Stride Threat Model is one of the best threat modeling methodologies available. It puts forward a framework that is most widely used to access cybersecurity. It also demands to identify and classify threats by nature of their attack under 6 heads namely – Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service DoS, and Elevation of privilege. Cyber experts choose the STRIDE threat model above many other threat modeling approaches because of its many benefits.
Read more about other Best Threat Modeling Methodologies.
STRIDE threat modeling will help you better prepare for future threats. It can organize many possible threats.
Threat modeling is a complex process that requires real-time data collection and analysis and a quick (if not real-time) response.
The Certified Threat Modeling Professional (CTMP) is a vendor-neutral course and certification program. In fact, the course curriculum will also focus on Security requirements in agile environments, Agile Threat modeling, Threat Modeling as Code, and Secure Design Principles to help you ensure security in the design phase.
Also Read, Integrating STRIDE Threat Model with DevOps



0 Comments